When you create an “Internal Network” in VirutalBox, three things happen behind the scenes.
- VirtualBox creates a virtual switch
- The VM gets a virtual network adapter, just like a real NIC.
- A virtual network cable connects the VM’s adapter to the virtual switch.
Think of it like the image below, where computers connect their network ports to the switch using CAT6 cables.

You can see I created a switch with the name of “mynetwork”. You attach any other VMs to the same switch by using the same name. Ensure the spelling is correct or you’ll be creating a different switch.
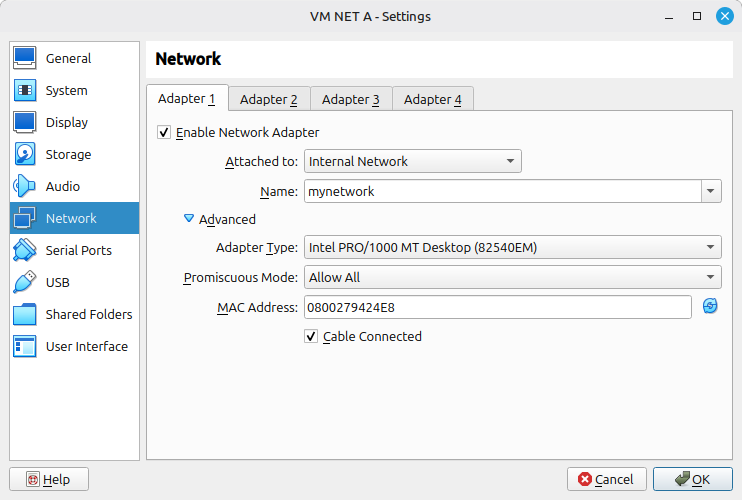
To figure out which interface it is, match the MAC address. In Virtualbox, my network adapter’s MAC is 0800279424E8.
In your Linux VM, run the command ip link.
owner@host:~$ ip link
1: lo: <LOOPBACK, UP, LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN mode DEFAULT group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
2: enp0s3: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc FQ_CODEL state up mode DEFAULT group default qlen 1000 link/ether 08:00:27:94:24:e8 brd ff:ff:ff:ff:ff:ff
owner@host:~$In this example, the interface enp0s3 has that MAC, so this is the one you would assign an IP address to.
Pro tip:
A physical network card has a hardware MAC filter. Your network card only accepts frames addressed to its own MAC address, broadcasts, and multicasts it subscribes to. Any other frame it sees on the wire gets dropped. In VirtualBox this is “deny all” under promiscuous mode, which is the default. This is correct and how a network should operate.
In certain situations, you may need to turn off this hardware MAC filter. In VirutalBox, you would set promiscuous mode to “Allow All”. Now when your virtual network card sees a frame on the wire from the switch, it will send it up the stack without filtering it.
Examples:
- Packing sniffing with Wireshark for traffic not destined to your own system.
- The VXLAN tunnel endpoints (VTEP) are accepting frames for devices across the network. The destination MAC won’t match the VTEP so unless you set “Allow All” your network card will drop the frame.